Call a private API
Glenn Gillen
VP of Product, GTM
Wouldn't it be nice to be able call a private API that's only available inside your private network, with a simple Snowflake procedure call? Wouldn't it be even better if it was not necessary to manage IP allow lists, open firewall ports, or setup services like PrivateLink? Would you believe me if I told you that it would take you less than 15 minutes to setup?
Introducing the Snowflake Call Private API Connector!
Snowflake 💙 APIs
Many services offer a HTTP API in addition to a web interface. This makes data retrieval from the command-line very easy, using a
simple curl command.
Snowflake is The Data Cloud and the place to support workloads such as data warehouses, data lakes, data science / ML / AI, and even cybersecurity. This centralization brings a huge amount of convenience through breaking down data silos and allowing teams to make smart data-informed decisions.
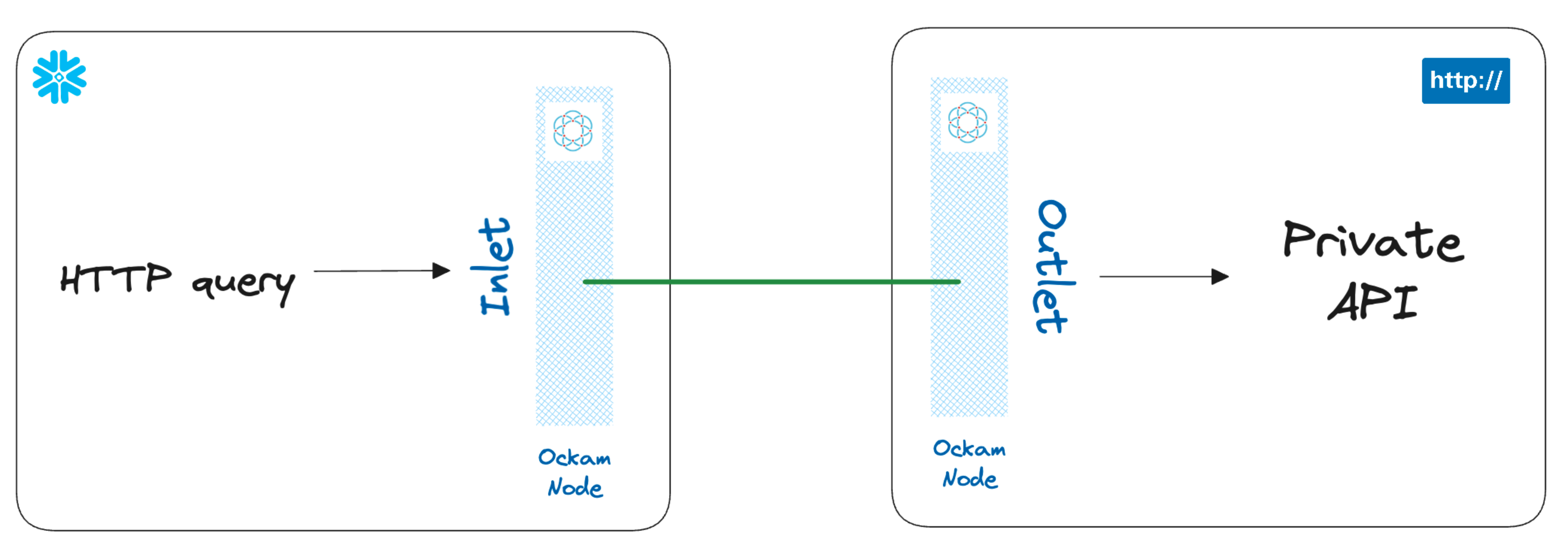
You might wonder though how it can be possible to tap into HTTP services from Snowflake applications, if those services are hosted in private networks. You might also wonder if it is possible to join the results of a remote call with one of your database tables as if the remote data was available as a local table.
In this post I'm going to show you how to securely access a private API, hosted in a private network, in just a few minutes. We will:
- Install and configure the Call private API connector.
- Make a stored procedure call to retrieve data as if it was a table select.
- Make a stored procedure call to post data to the API.
Install and configure the Call private API Connector
We are now going to create a set of stored procedures and a portal to access your private API.
Get the app
The Call private API Connector by Ockam is available in the Snowflake Marketplace - FIXME.
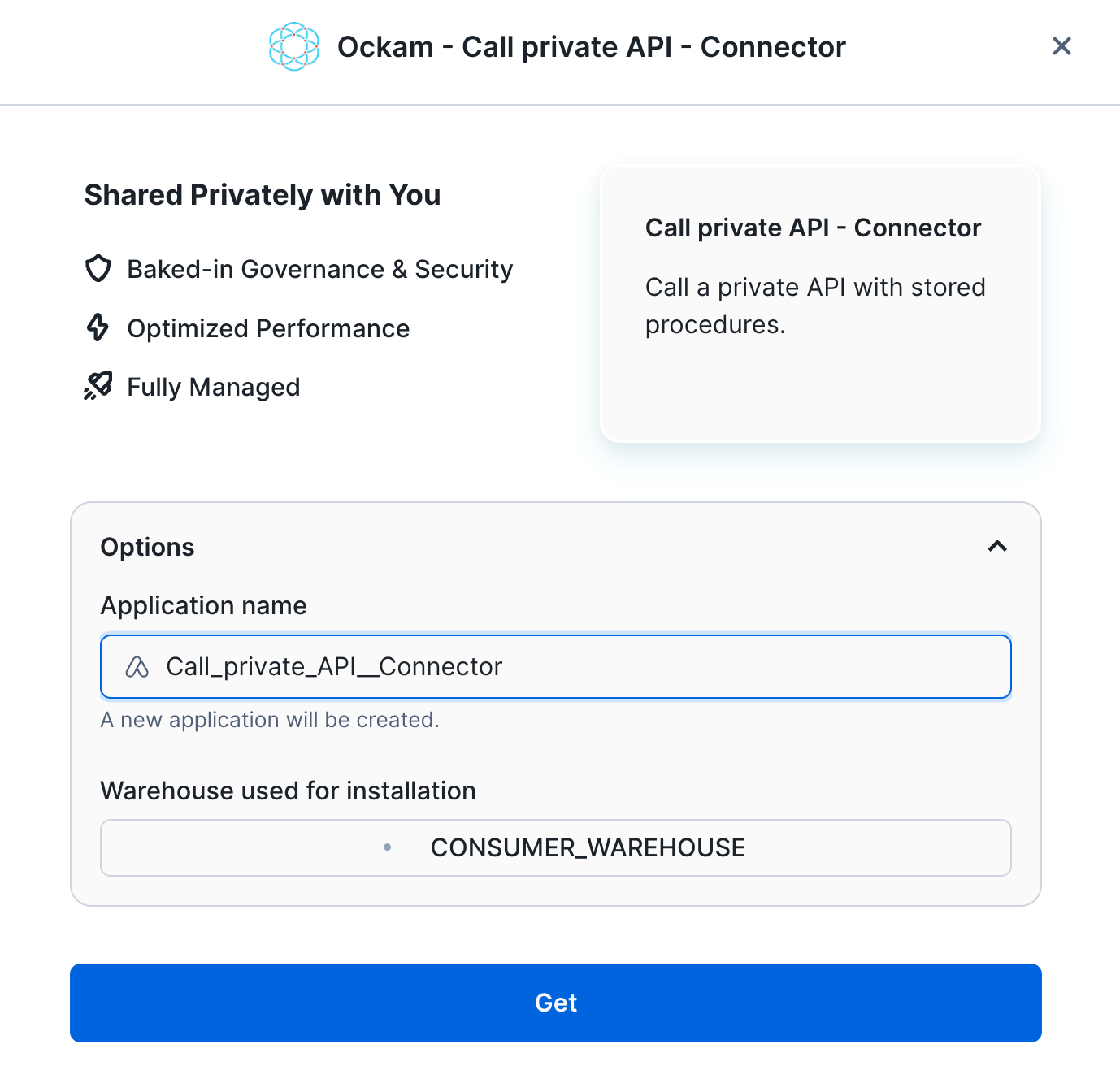
Select a warehouse
The first screen you're presented with will ask you to select the warehouse to utilize to activate the app and can choose to change the application name.
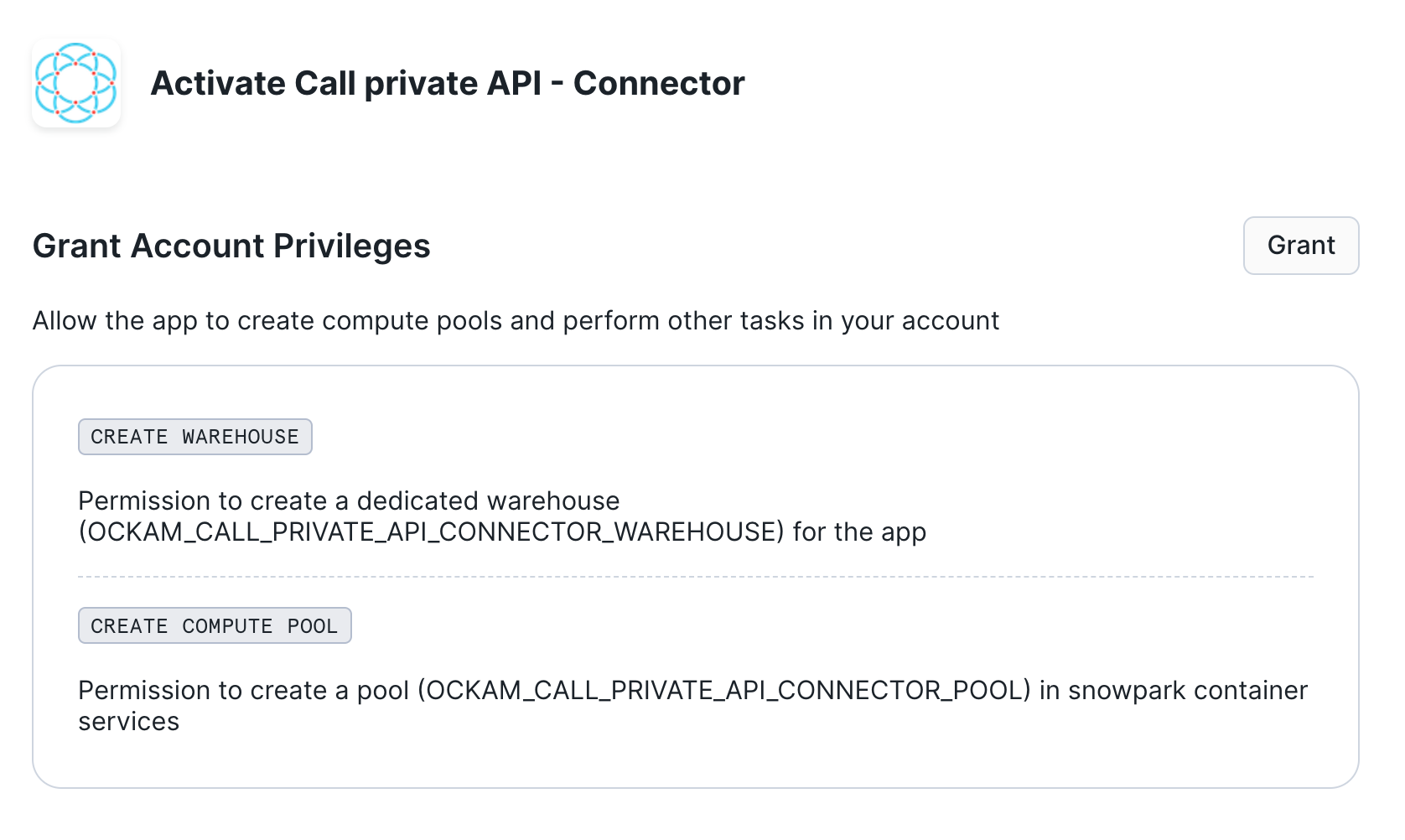
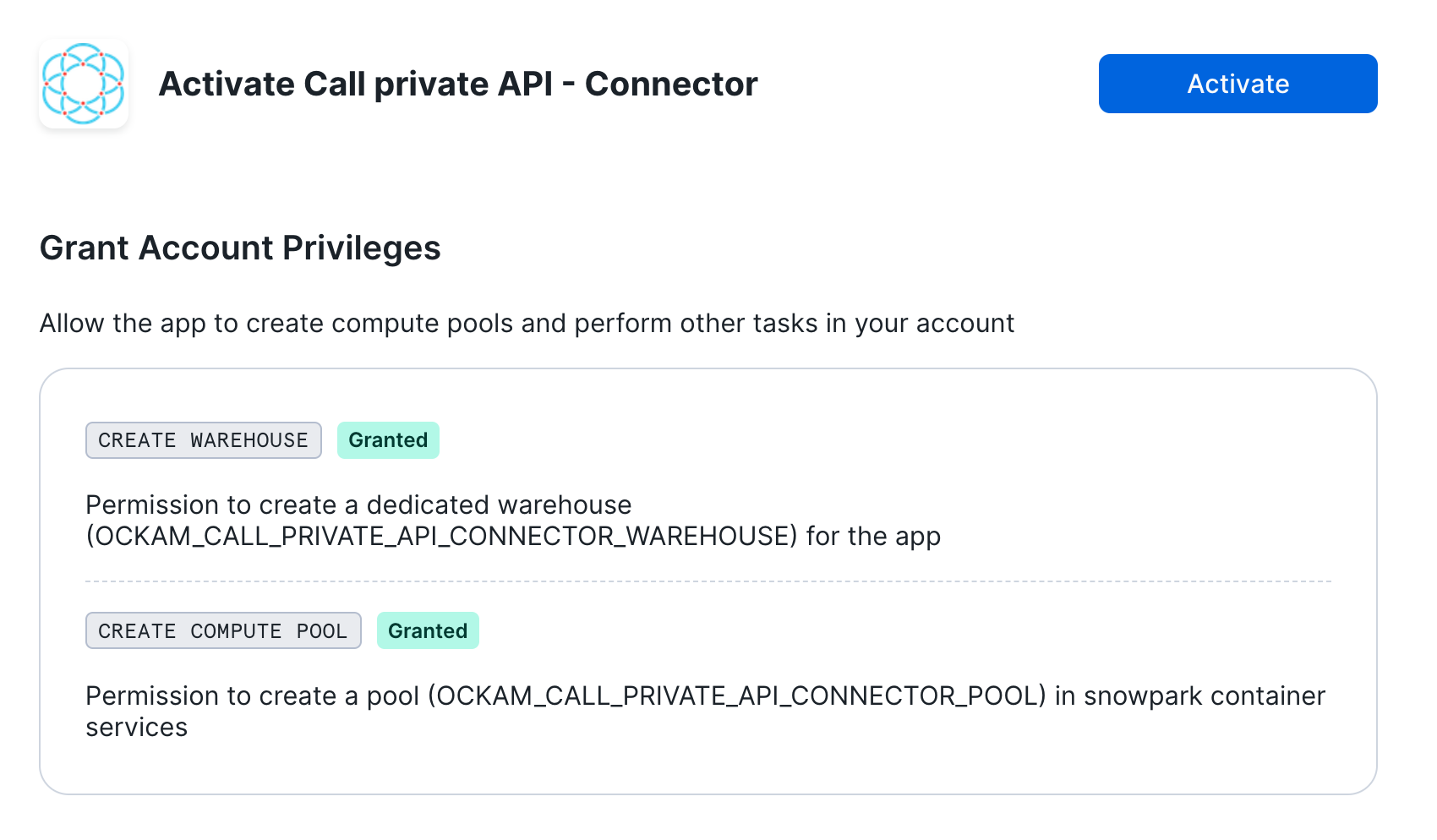
Grant account privileges
Click the Grant button to the right of this screen. The app will then be
automatically granted permissions to create a warehouse and create a compute
pool.
Activate app
Once the permissions grants complete, an Activate button will appear. Click
it and the activation process will begin.
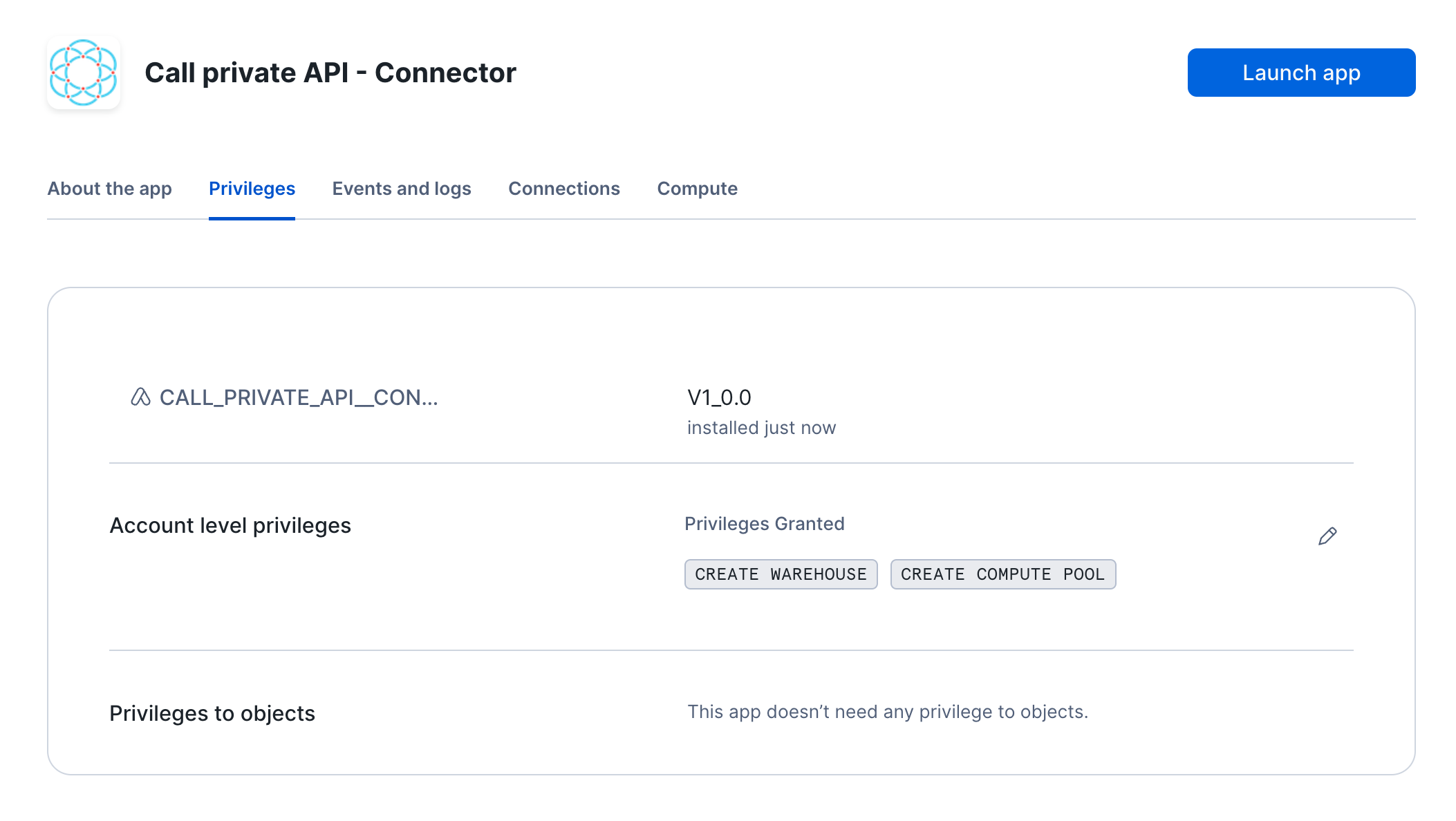
Launch app
After the app activates you'll see a page that summarizes the
privileges that the application now has. There's nothing we need
to review or update on these screens yet, so proceed by clicking the Launch app button.
Configuration
We are now going to configure the application. We first need to:
- Create an Ockam project and issue an enrollment ticket
- Configure the user name and password which will be used to access the server.
Configuring the application
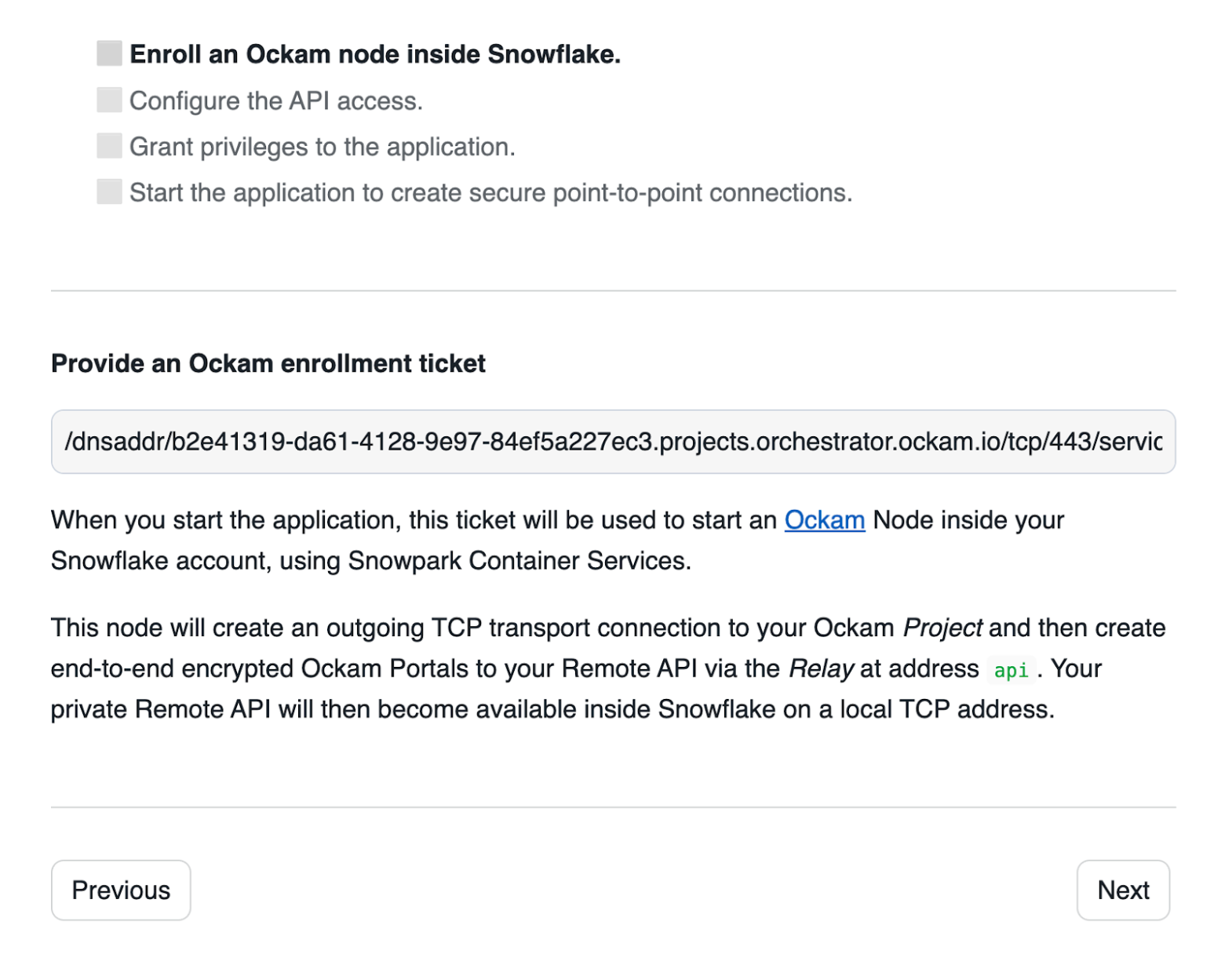
Configure connection details
Click "Get started" to open the Snowflake setup screen.
Take the contents of the file snowflake.ticket that we just created and paste
it into "Provide the above Enrollment Ticket" form field in the "Configure app"
setup screen in Snowflake.
Configure API access
In this screen we need to select an authorization method. For this tutorial you
can select Digest and continue. The other options available to use are:
NoneNo credentials are required to access the private API.BasicThe private API is accessible with a user name and password.DigestThe private API is accessible with a user name and password, but they are not transmitted in clear text.Bearer tokenThe private API is accessible with a token passed with anAuthorizationheader.API KeyThe private API is accessible with an API Key passed with a specific extension header (for exampleX-api-key).
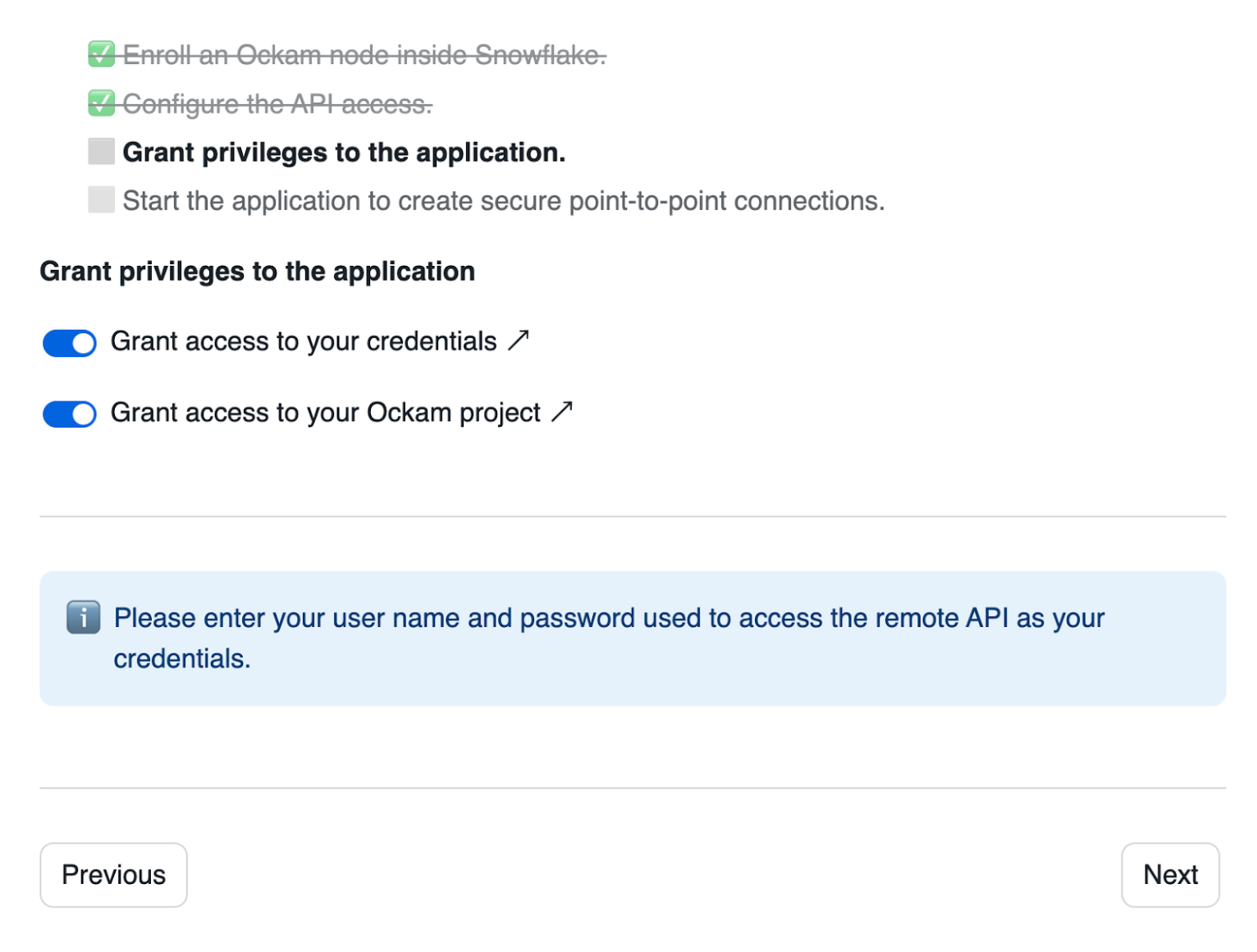
Grant privileges
To be able to authenticate with Ockam Orchestrator and then discover the route to our outlet, the Snowflake app needs to allow outbound connections to your Ockam project.
Toggle the Grant access to your credentials button, enter user for the user name and password for the user password.
Toggle the Grant access to your Ockam Project button and approve the connection by
pressing Connect.
Start the application
Press "Next" and wait for the application to start. Once started, you should be able to see the server logs.
You can also notice a tab containing the logs for an Ockam node. That Ockam node is a portal inlet:
- Which accesses a relay named
apiin the Ockam project. - Declares that only services with the attribute
apican be connected to the inlet.

Setup an Ockam outlet on the API side
Testing the connection
Next steps
In summary, we are now able to securely access a private API, using Snowflake stored procedures, without exposing any port to the internet.
If you'd like to explore some other capabilities of Ockam I'd recommend:
- Creating private point-to-point connections with any database
- Adding security as a feature in your SaaS product
Previous Article
How to build in security as a SaaS feature
Next Article
Authenticate & authorize every access decision